Integration guide for FreePBX v15
FreePBX supports WebRTC. This will guide you through the steps to enable a websocket on FreePBX.
Requirements
Server Side versioning
| Component | Minimum Version |
|---|---|
| Asterisk | 11.5 |
| Certificate Manager | 12.0.0alpha1 |
| Core | 12.0.1beta9 |
| User Control Panel | 12.0.0beta7 |
| FreePBX | 12.0.1beta34 |
Install a certificate with your domain (not self-signed)
- From the top menu click Admin
- In the drop down click Certificate manager
If you don’t have a certificate yet, generate a Certificate Signing Request and apply for a certificate.
When you al ready have a certificate you can upload the certificate and click Generate Certificate:
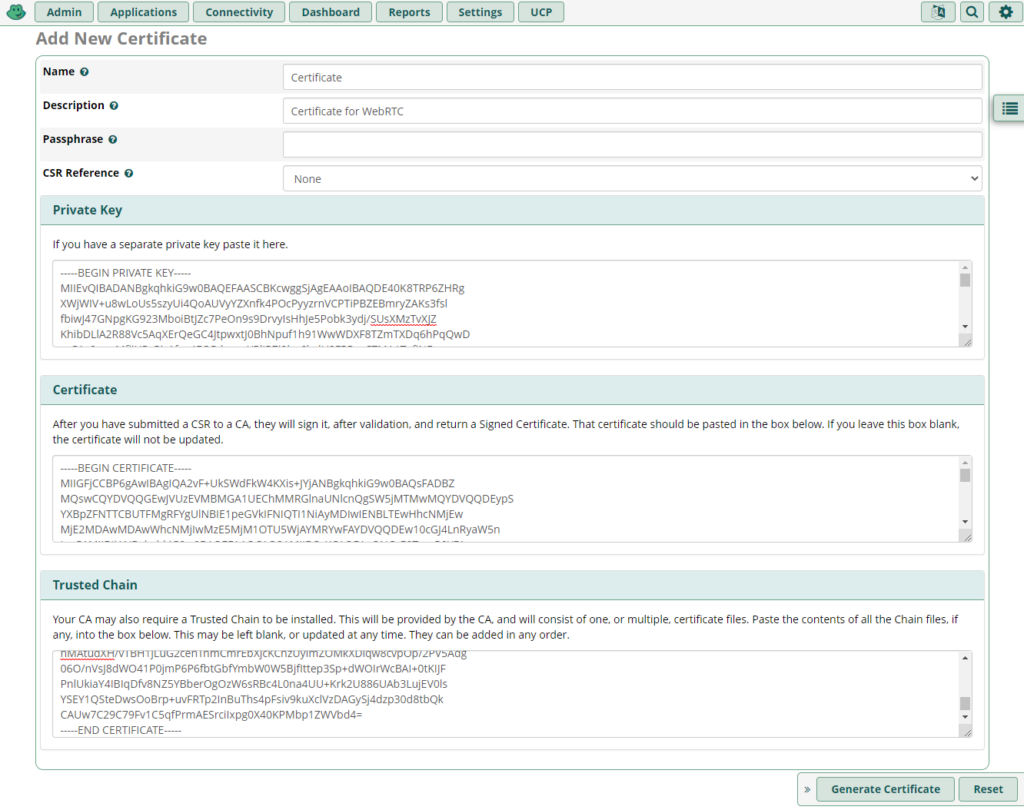
Set the certificate as default (if you wish)
Restart Asterisk and check if the websocket is running
By navigating to Admin–>Asterisk CLI
Restart Asterisk:
Send the command “core restart now”
Check if the websocket is listening:
Send the command “http show status”

Enabling WebRTC Phone for an extension
- Click Admin
- Click Extensions
- Create or edit an extension
- Go to tab advanced and make sure you make the following changes:
- Enable AVPF
- Enable ICE Support = YES
- Enable rtcp Mux = YES
- Media Encryption = DTLS-SRTP
- Save the extensions en click Apply Config.
Adding the websocket server to the management portal.
Enter your domain in the management pane.
Adjust firewall and portforwarding when behind NAT
If the PBX is running behind NAT, please make sure you setup port forwarding and allow inbound traffic to the internal server. WebRTC uses UDP ports (10000-65535) Also note that you need a STUN server for WebRTC to make two way communication possible.
For example; when running FreePBX behind NAT on the public IP 123.123.123.123 and the private IP 10.10.10.231
Forward TCP port 8089 to 10.10.10.231 in your router.
Adjust NAT settings (Settings–>SIP Settings):

Add a STUN server to Asterisk (Settings–>SIP Settings):

Setup the ICE Host Candidate:
10.10.10.231=>123.123.123.123

Internal domainname
When you need to use the WebRTC client behind the same WAN, you can create an internal DNS mapping pointing towards your server, so the traffic will stay internal.
For example when you use webrtc.company.xys A 10.10.10.231
Or you can use a rewrite mechanism in Pi.hole or Adguard.
